Did you know that in 2024, over 60% of all reported data breaches involved unsecured documents? As digital threats grow more sophisticated, safeguarding information is no longer optional. This guide explores every essential aspect of document protection for 2025, equipping you with actionable strategies to stay ahead of evolving risks.
We’ll uncover the latest threats, proven protection strategies, cutting-edge encryption, access management best practices, compliance essentials, and future trends. Don’t wait until your organization faces the consequences of poor document protection—discover how to secure your critical files now.
The Evolving Landscape of Document Protection in 2025
In 2025, document protection is facing a rapidly changing threat landscape. Organizations of all sizes are under pressure to adapt as cybercriminals deploy more advanced tactics. The rise of remote work, the increase in document diversity, and shifting regulations are reshaping how businesses must think about securing their sensitive information.
Key Trends and Threats
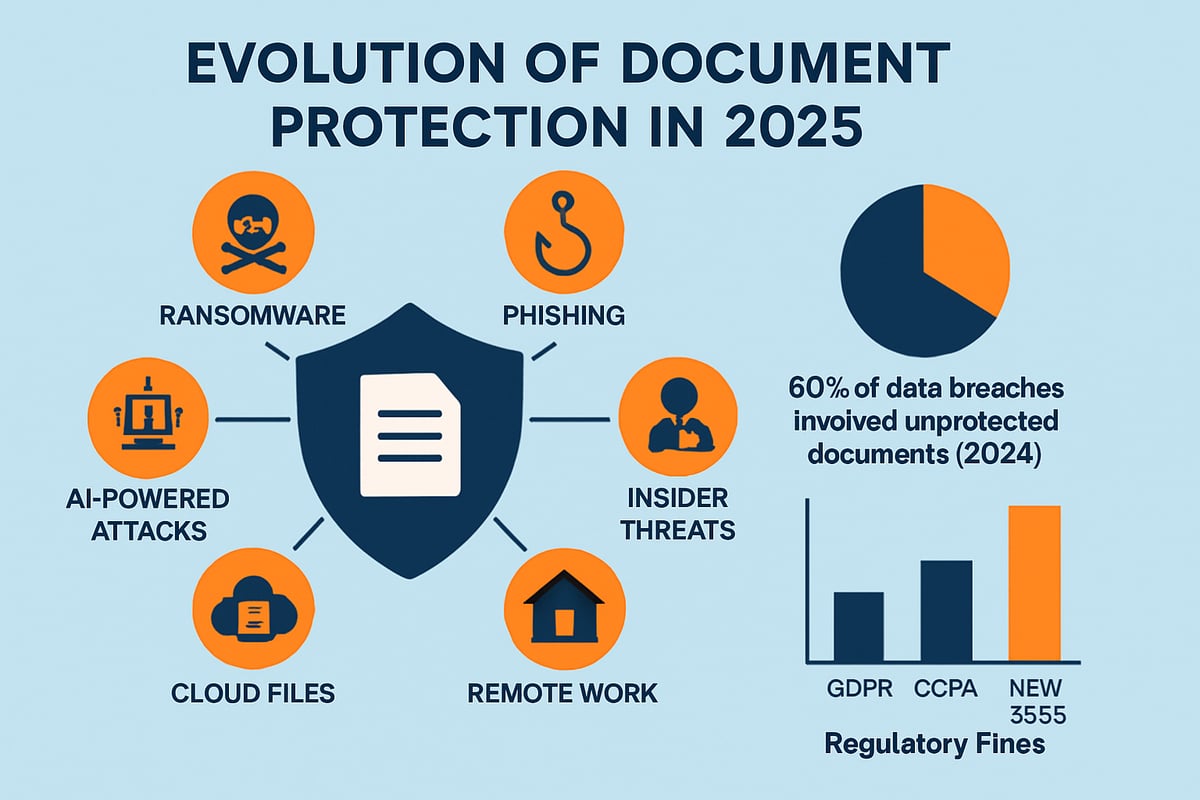
The threat landscape for document protection is evolving at an unprecedented pace. Cybercriminals are no longer relying solely on brute force; instead, they use sophisticated ransomware strains, highly targeted phishing campaigns, and even insider attacks to compromise confidential files.
The shift to remote and hybrid work models has expanded the attack surface. Employees now access sensitive documents from home networks and personal devices, increasing the risk of unauthorized exposure. At the same time, the proliferation of document formats—PDFs, DOCX files, and cloud-native documents—introduces unique vulnerabilities. Each format demands specific security controls, and gaps can easily be exploited.
Recent high-profile document leaks have highlighted the real-world impact. For example, in 2024, over 60% of data breaches involved unprotected documents, according to leading industry reports. These breaches led to millions in damages and eroded public trust in affected organizations.
Regulatory pressures are also intensifying. Compliance with GDPR and CCPA is no longer optional, and new 2025 laws are raising the bar for document protection. Organizations must now demonstrate not just intent but active enforcement of security protocols.
Another major trend is the rise of AI-powered attacks. Malicious actors are leveraging artificial intelligence to bypass traditional security measures, automatically detect weaknesses, and adapt to changing document protection strategies. For a more detailed look at these trends and their implications, see Document Security and 10 Trends You Should Know in 2025.
| Threat Type | Description |
|---|---|
| Ransomware | Encrypts documents and demands payment |
| Phishing | Tricks users into revealing document access |
| Insider Attacks | Employees or partners mishandle documents |
| AI-Driven Attacks | Uses machine learning to bypass defenses |
The Cost of Inadequate Document Protection
Failing to prioritize document protection comes with serious consequences. The financial toll can be staggering—data breaches and intellectual property theft often result in direct losses, regulatory fines, and costly legal settlements.
Reputational damage is another critical factor. Customers lose confidence when their data is mishandled, which can lead to lost business and long-term brand erosion. Legal ramifications are equally severe; organizations found non-compliant with privacy laws face lawsuits and penalties.
There are also hidden costs to consider. Operational disruptions can stall productivity, while loss of competitive advantage can be difficult to recover. Case studies from the past year have shown companies penalized not just by regulators, but also by the marketplace for mishandling sensitive documents.
In summary, document protection is no longer a checkbox—it's a core business priority that impacts every aspect of organizational resilience and success.
Core Principles and Methods of Document Protection
Protecting your organization’s documents is no longer optional. In 2025, robust document protection is essential for safeguarding sensitive data, maintaining compliance, and preventing costly breaches.
Understanding the foundational methods of document protection empowers you to create a secure environment that adapts to new threats. Let’s explore the core principles every organization should implement.
Restricting Document Modification
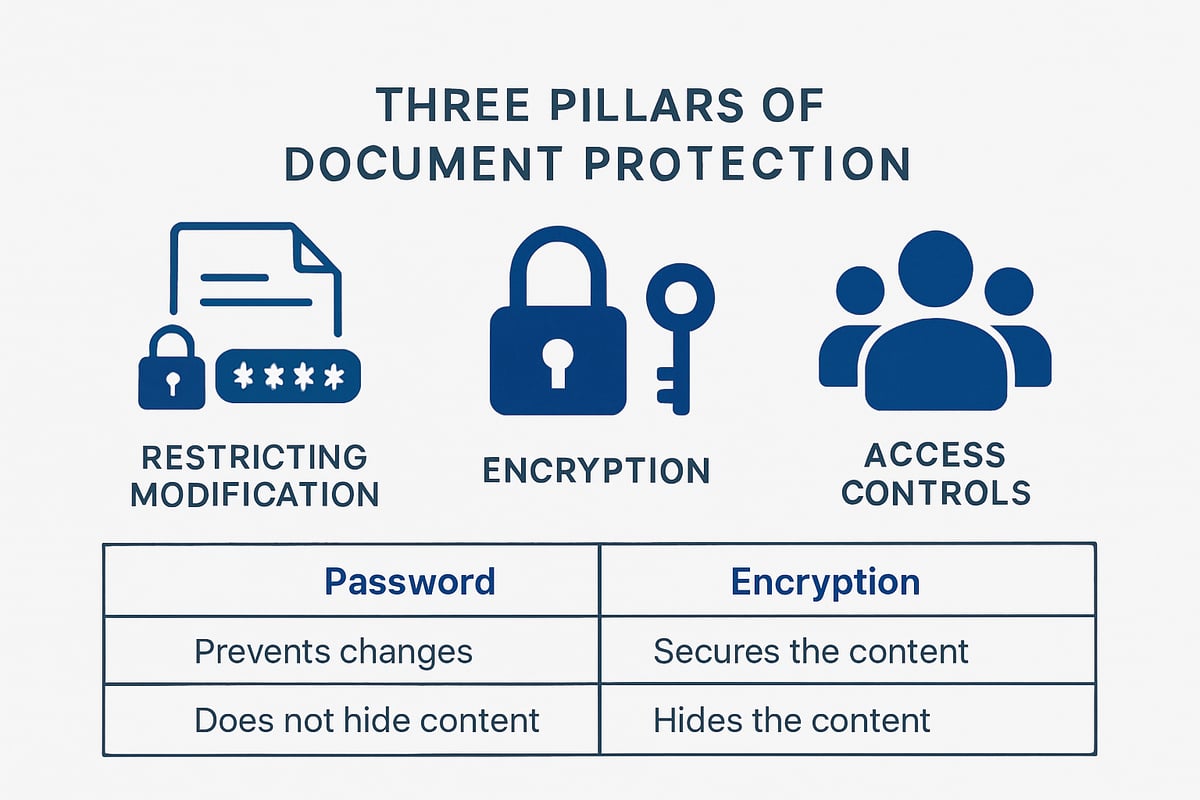
One of the primary objectives of document protection is to prevent unauthorized changes to files. Restricting document modification helps preserve data integrity and ensures only approved users can make edits.
Common modification restriction techniques include:
- Password protection: Require a password to open or change a document.
- Editing restrictions: Limit who can edit, comment, or format content.
- Section-based protection: Protect specific parts of a document while leaving others editable.
- Read-only and protected view: Allow users to view but not alter files.
- Audit trails and change tracking: Record every modification for accountability.
For example, Microsoft Word offers built-in document protection features and APIs that let administrators enforce editing restrictions and monitor changes. According to recent vendor surveys, 75% of organizations now use some form of document modification restriction as part of their document protection strategy.
By leveraging these tools, you create multiple layers of defense, reducing the risk of accidental or malicious changes.
Encryption: The Foundation of Secure Documents
Encryption is the cornerstone of document protection. While password protection limits access, encryption actually scrambles file contents, making them unreadable without the correct key.
There are several types of encryption:
- At-rest encryption: Protects documents stored on devices or servers.
- In-transit encryption: Secures files as they move across networks.
- End-to-end encryption: Ensures only intended recipients can decrypt content.
| Protection Method | What It Does | Example Use Case |
|---|---|---|
| Password Protection | Blocks unauthorized access | Opening a PDF or Word doc |
| Encryption (AES-256) | Secures content even if file is stolen | Cloud storage, email attachments |
Modern standards like AES-256 and RSA are vital for document protection, providing strong security for sensitive files. Many Office and PDF editors now include built-in encryption options, making it easier to safeguard documents during storage and sharing.
Legacy encryption methods may no longer be sufficient in 2025. Regularly updating your encryption practices is crucial to keep pace with evolving threats.
User Permissions and Access Controls
Fine-tuned access management is at the heart of effective document protection. Assigning granular permissions lets you control exactly who can view, edit, or share documents.
Key access control methods:
- Role-Based Access Controls (RBAC): Assign permissions based on user roles or departments.
- Group and individual permissions: Tailor access for teams or specific users.
- External sharing controls: Manage guest access and set expiration dates for shared links.
- Audit logs: Track who accessed or modified each document.
Platforms like Google Workspace and Microsoft 365 make it simple to set permissions and monitor access. For deeper insights, 15 Best Practices for Document Management Security offers actionable tips on strengthening permission structures and conducting regular audits.
By actively managing who can access and interact with documents, you reduce the risk of leaks and maintain compliance with privacy regulations.
Advanced Document Protection Technologies in 2025
The landscape of document protection is rapidly transforming as organizations face new, more sophisticated threats. In 2025, advanced technologies are redefining how sensitive files are secured, accessed, and monitored. Understanding these innovations is essential for anyone responsible for safeguarding critical information.
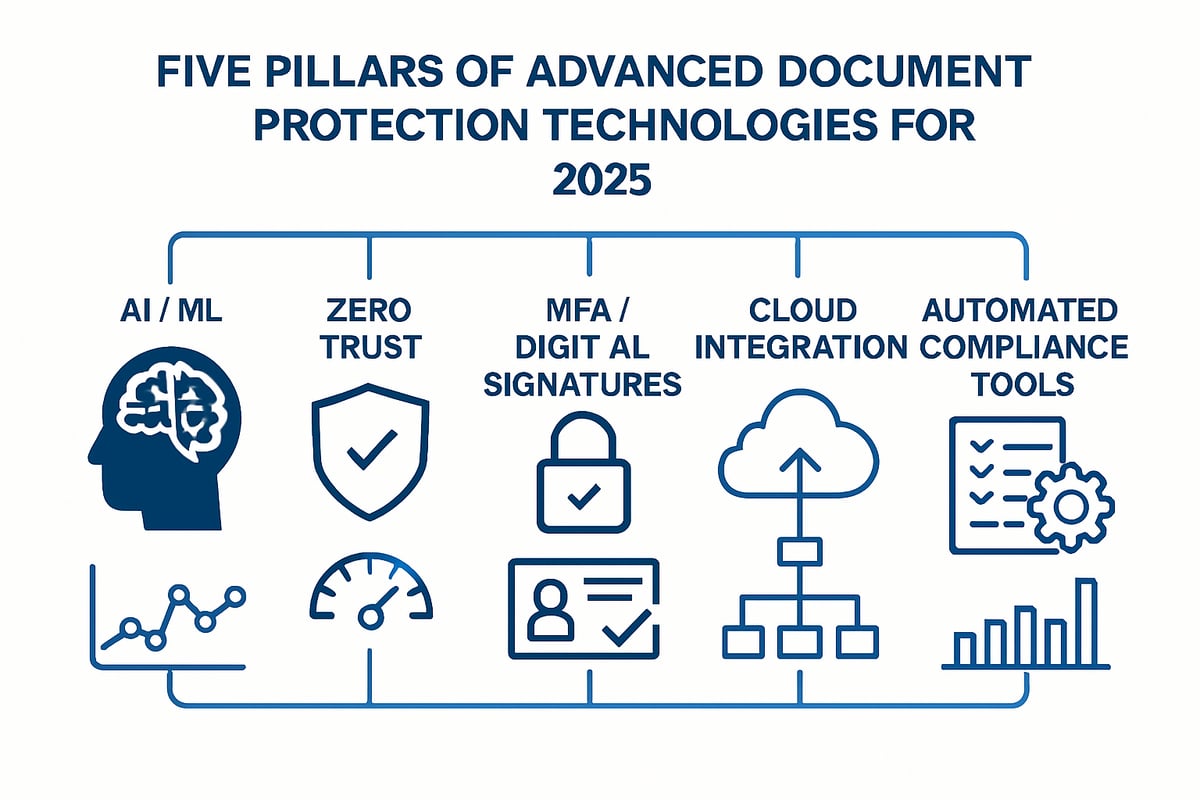
AI and Machine Learning for Threat Detection
AI and machine learning have become central to modern document protection. These systems analyze user behavior and document access patterns in real time, identifying anomalies that may signal a security threat.
- AI detects unusual downloads, edits, or sharing activity.
- Machine learning adapts to new attack vectors, even as cybercriminals evolve their tactics.
- Automated alerts notify security teams of suspicious document events.
For example, an AI-driven platform might flag an employee attempting to download sensitive files outside business hours or from an unfamiliar device. This proactive approach allows organizations to react swiftly, minimizing the risk of data loss.
Zero Trust Security for Documents
Zero trust is now a cornerstone of document protection. This model requires every user and device to be continuously verified before accessing documents, regardless of their network location.
Key principles include:
- Never trust, always verify: Authenticate every access attempt.
- Least privilege: Limit document access to only those who need it.
- Micro-segmentation: Isolate sensitive files within secure zones.
In practice, zero trust policies can be integrated with adaptive access controls, ensuring that only authorized users can interact with specific documents. For a detailed overview of zero trust strategies and their role in document protection, see Data Security Best Practices for 2025.
Multi-Factor Authentication (MFA) and Digital Signatures
Multi-factor authentication adds a crucial layer to document protection, requiring users to verify their identity through at least two methods before accessing or editing files.
- Common MFA methods: SMS codes, authenticator apps, hardware tokens.
- Digital signatures: Provide authenticity and non-repudiation for critical documents.
For instance, modern contract workflows often require a legally binding e-signature, coupled with MFA, to ensure only the intended recipient can sign. This combination greatly reduces the risk of unauthorized document access or tampering.
Integrating Document Protection with Cloud and Collaboration Platforms
Cloud and collaboration platforms are at the heart of modern work, making document protection more complex and essential than ever. Leading platforms such as Microsoft 365, Google Workspace, and Box have introduced advanced security features.
- Real-time co-authoring with end-to-end encryption.
- Granular access controls for internal and external sharing.
- Unified management across hybrid and multi-cloud environments.
These capabilities empower organizations to collaborate securely while maintaining strict oversight of all document activities. Seamless integration ensures that security is not an obstacle to productivity.
Automated Compliance and Audit Tools
Regulatory demands are increasing, and automated compliance tools are now vital for effective document protection. These tools monitor document policies, generate audit trails, and issue real-time alerts for potential violations.
- Continuous compliance checks reduce manual errors.
- Detailed audit logs support investigations and regulatory reporting.
- Automated alerts help organizations respond quickly to suspicious activities.
By leveraging these technologies, organizations can maintain compliance with evolving data privacy laws and demonstrate accountability during audits. Automated compliance solutions have become indispensable for robust document protection in 2025.
Step-by-Step Guide to Implementing Document Protection
Securing your organization’s confidential information starts with a structured approach. Implementing document protection is not just about using the right tools—it’s about understanding your needs, building strong policies, applying effective measures, and cultivating a security-first culture.
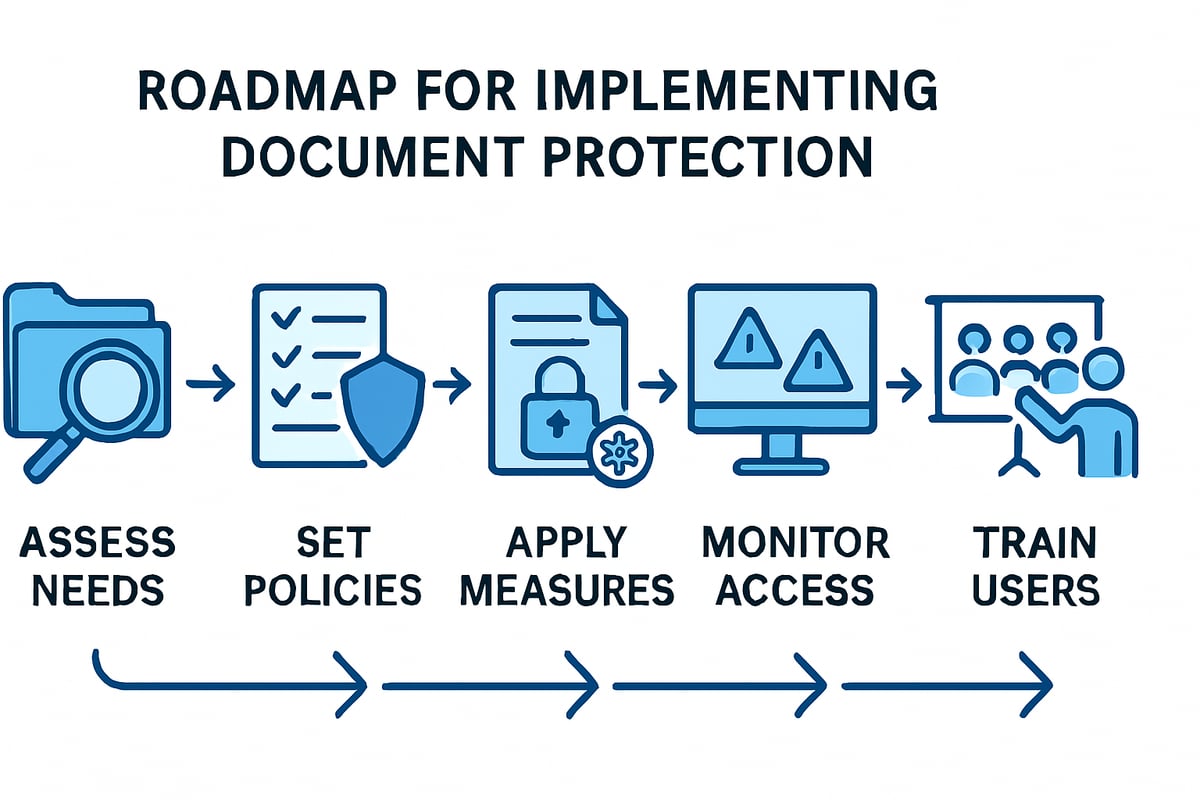
Assessing Document Security Needs
Begin by inventorying all document types across your business. Identify which files are most sensitive—think financial records, client contracts, or internal strategies. Pay close attention to where documents are stored: local drives, network shares, or cloud platforms.
Next, evaluate regulatory and business requirements. Are you subject to GDPR, CCPA, or industry-specific mandates? Map out how documents flow between departments and third parties.
A simple table can help clarify priorities:
| Document Type | Sensitivity Level | Storage Location | Compliance Requirement |
|---|---|---|---|
| Financial Reports | High | Cloud Drive | GDPR, SOX |
| HR Records | Medium | Internal Server | GDPR, CCPA |
| Marketing Assets | Low | Shared Network | None |
Understanding your landscape is foundational to effective document protection. This assessment ensures your next steps are targeted and efficient.
Setting Up Document Protection Policies
Once you know what needs protecting, define clear document protection policies. Decide who can access, edit, and share each document type. Specify rules for both internal teams and external collaborators.
Establish a document classification system. For example:
- Confidential: Only executives and HR
- Internal Use: All employees
- Public: Clients and partners
Document these rules in an accessible policy manual. Outline procedures for requesting access or sharing files outside the company. These guidelines set expectations and reduce the risk of unauthorized exposure.
Consistent policies are the backbone of document protection. They support compliance, streamline audits, and maintain operational integrity.
Applying Protection Measures
With policies in place, it’s time to apply document protection measures. Start by enabling password protection and encryption in your preferred tools. For Microsoft Word:
File > Info > Protect Document > Encrypt with Password
For PDFs, use your editor’s security tab to restrict opening, editing, or printing. Cloud platforms like Google Workspace let you set permissions for viewers, commenters, and editors.
Section-level protection is valuable for collaborative files. Assign edit rights only where necessary. To see a comprehensive, multi-layer approach—including access controls and resilience—review Document Protection Done Right in 2025 & Beyond.
Consistently applying these measures is vital for robust document protection.
Managing and Monitoring Document Access
Effective document protection continues after initial setup. Set up access logs to track who opens, edits, or shares files. Enable real-time alerts for unusual activity—such as repeated failed login attempts or unexpected downloads.
Regularly review and update access rights. Remove permissions for users who’ve changed roles or left the organization. Automated tools can simplify monitoring, ensuring no unauthorized access goes unnoticed.
Periodic audits help confirm your document protection strategy is working. This vigilance preserves confidentiality and demonstrates compliance.
Training and Educating Users
No document protection system is complete without user education. Train employees to recognize phishing attempts and avoid suspicious links. Simulate attacks to test responses and reinforce best practices.
Key training elements include:
- Identifying sensitive documents
- Using secure sharing methods
- Responding to security incidents
- Reporting suspicious activity promptly
Regular awareness programs foster a culture where everyone contributes to document protection. Empowered users are your first line of defense.
Ensuring Compliance and Meeting Regulatory Requirements
Navigating the complex landscape of compliance is essential for robust document protection. In 2025, organizations must stay ahead of evolving data privacy laws and ensure their document protection aligns with global mandates. The consequences of non-compliance can be severe, making a proactive approach vital to safeguard sensitive information and maintain trust.
Understanding Regulatory Obligations
Organizations face a growing number of regulations impacting document protection. Key laws include GDPR in Europe, CCPA in California, HIPAA in healthcare, and new 2025 privacy regulations emerging globally. Each regulation brings unique requirements for how documents are handled, stored, and accessed.
Consider these core compliance areas:
- Document retention: How long must data be kept and when should it be destroyed?
- Encryption standards: What level of encryption is required for stored and transmitted documents?
- Access controls: Who can view, edit, or share protected documents?
A quick comparison helps clarify major mandates:
| Regulation | Retention | Encryption | Access Controls |
|---|---|---|---|
| GDPR | Yes | Strong | Strict |
| CCPA | Yes | Required | User consent |
| HIPAA | Yes | Mandatory | Role-based |
| 2025 Laws | Evolving | Advanced | Continuous |
Understanding these obligations is crucial for effective document protection strategies.
Implementing Compliance-Driven Document Protection
To achieve compliance, organizations must align document protection with legal requirements. This means building policies that reflect both business needs and regulatory expectations. Start by classifying documents based on sensitivity and legal mandates.
- Define access rights for each document type.
- Use strong encryption for all sensitive files.
- Maintain audit trails to track access and changes.
Regular audits and documentation help prove compliance. Preparing for a compliance audit involves organizing policies, logs, and evidence of document protection. For inspiration, review how OdysseyGPT privacy policy overview demonstrates transparency and commitment to privacy, which can guide your own compliance efforts.
By embedding compliance into every layer of document protection, organizations reduce risks and build trust with customers and regulators.
The Role of Automated Compliance Tools
Automated tools are transforming document protection in 2025. These solutions monitor document access, enforce protection policies, and generate real-time compliance reports. By reducing human error, automation ensures continuous alignment with evolving regulations.
Key benefits include:
- Instant alerts for unauthorized document access.
- Automated retention and deletion schedules.
- Comprehensive audit trails for every document event.
Integrating automated compliance tools streamlines reporting and makes it easier to respond to regulator requests. This proactive approach strengthens document protection and frees up valuable resources for strategic initiatives.
Future Trends and Innovations in Document Protection
As we look to the future, document protection is set to undergo a dramatic transformation. New threats and regulatory pressures are pushing organizations to adopt advanced technologies that keep pace with evolving risks. The innovations below will redefine how sensitive information is secured and managed in 2025 and beyond.
AI-Powered Adaptive Security
AI is rapidly reshaping document protection by enabling real-time, adaptive defenses. Modern AI systems can analyze access patterns, flag anomalies, and predict potential breaches before they occur. These tools use behavioral analytics to assign risk scores to users and documents, allowing security teams to focus on the most critical threats. Adaptive policies adjust access or encryption levels dynamically, reducing exposure without manual intervention. For example, AI can block a suspicious login or limit downloads if unusual activity is detected. As highlighted in Introducing OdysseyGPT security features, integrating AI-driven protection is now essential for any organization seeking robust document protection.
Decentralized and Blockchain-Based Document Protection
Decentralized systems and blockchain are introducing new levels of trust and transparency to document protection. By recording every access or modification on an immutable ledger, blockchain ensures document integrity and provides a clear audit trail. Smart contracts automate permissions and verification, granting access only to authorized users and logging every transaction. This approach is especially valuable for industries dealing with high-value intellectual property or sensitive legal documents. Blockchain-based document protection minimizes the risk of tampering, makes audits more efficient, and gives organizations a powerful tool for compliance and investigation.
Privacy-Enhancing Technologies (PETs)
Privacy-enhancing technologies are emerging as a cornerstone for document protection, especially in regulated sectors. Techniques like homomorphic encryption and secure multi-party computation allow organizations to process and analyze sensitive documents without exposing raw data. For example, financial services can run fraud detection algorithms on encrypted documents, while healthcare providers can share data insights without risking patient privacy. PETs are critical for meeting new privacy regulations and maintaining customer trust. To learn more about foundational security practices that complement these innovations, see Document security best practices.
The Rise of Self-Destructing and Watermarked Documents
Innovative features such as self-destructing and watermarked documents are becoming mainstream in document protection. Time-limited access or one-time viewing capabilities ensure that sensitive files cannot be stored or shared beyond their intended lifespan. Digital watermarks embed identifying information directly into documents, enabling organizations to trace leaks and hold individuals accountable. These technologies are particularly useful for contracts, intellectual property, and confidential communications, helping organizations prevent unauthorized distribution and quickly respond to incidents.
Preparing for Quantum-Resistant Document Security
Quantum computing poses a significant challenge to existing encryption methods, making quantum-resistant document protection a top priority for forward-thinking organizations. Cryptographers are developing new algorithms designed to withstand quantum attacks, ensuring long-term confidentiality. Steps to future-proof document protection include inventorying encrypted assets, updating cryptographic libraries, and monitoring developments in quantum-safe standards. Organizations should start planning now to avoid being caught off guard when quantum threats materialize.
Appendix: Glossary of Key Document Protection Terms
Understanding key terms is essential for mastering document protection. This glossary offers concise definitions to help you navigate the evolving landscape of secure document management in 2025.
| Term | Definition |
|---|---|
| Document Protection | Strategies, technologies, and practices used to secure documents from unauthorized access, alteration, or loss. |
| Encryption | The process of converting information into a coded format to prevent unauthorized access. Common in both at-rest and in-transit document protection. |
| Password Protection | Restricting document access or modification by requiring a password. Often combined with encryption for stronger security. |
| Multi-Factor Authentication (MFA) | A security method requiring two or more forms of verification before granting access to documents. |
| Role-Based Access Control (RBAC) | A system that grants permissions based on user roles, ensuring only authorized individuals can access or edit sensitive files. |
| Zero Trust | A security model that assumes no user or device is trusted by default, requiring continuous verification for document access. |
| Digital Signature | An electronic means of verifying document authenticity and integrity, legally binding in many jurisdictions. |
| Audit Trail | A chronological record of document activities—such as access, edits, or sharing—used for monitoring and compliance. |
| Protected View | A mode that opens documents in a read-only state, reducing the risk of malicious modifications or malware. |
| Compliance | Adhering to legal, regulatory, and industry standards for document handling, such as GDPR or CCPA. |
For those managing digital documents on business platforms, understanding web security principles is equally important. Learn more about web security for B2B platforms to strengthen your document protection strategy.
Familiarizing yourself with these terms will empower you to make informed decisions and implement stronger document protection measures in your organization.
As we’ve explored, protecting your documents in 2025 means staying ahead of evolving threats, mastering modern security tools, and keeping compliance top of mind. With OdysseyGPT, you don’t have to tackle this challenge alone—our platform empowers you to interact with your files, extract crucial data, and enforce advanced protections with ease. If you’re ready to transform your document security strategy and gain more control over your sensitive information, I encourage you to Start free trial. Experience firsthand how conversational AI can elevate your document protection today.